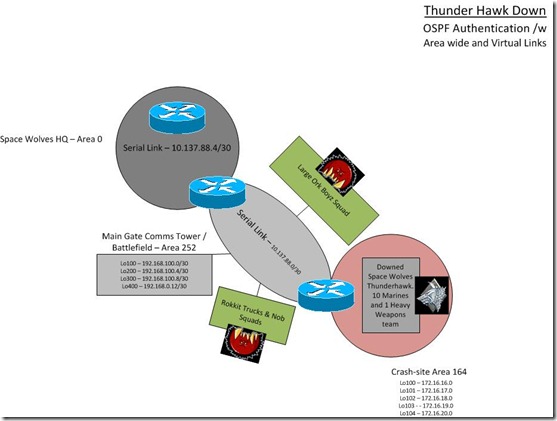
Today we go through the example of Thunder Hawk Down. Apologies for the slow reply. I had my engagement party on Saturday night and found myself busy getting ready last week.
Just recapping on the objectives.
Objectives
- – Configure RID’s/Interface IP’s and Loopbacks.
- – Establish an OSPF link from Space Wolves HQ Area 0 to Main Gate Comms Tower Area 252.
- – Secure the link with the strongest authentication possible.
- – Establish a Virtual link for Area 164 back to Area 0.
- – Secure the link.
- – Verify and inform the Icebane to hold on.
Step 1
Configure Router Hostnames and Line Console Parameters
Here under each router I configure the Hostname to allow for identification of devices. Under line con 0 I configure no exec-timeout. This means my console session will no log out. This is great for GNS3 as idle-pc values stop working and my CPU maxes to 100%. Never use no exec-timeout in a production environment. Logging synchronous stops console messages from interrupting you whilst you type.
HQ
hostname HQ
line con 0
no exec-timeout
logging synchronous
MainGate
hostname MainGate
line con 0
no exec-timeout
logging synchronous
Icebane
hostname Icebane
line con 0
no exec-timeout
logging synchronous
Step 2
Configure Interface IP addresses and Loopbacks
Here I have configured the IP addresses according to the scheme. I have added descriptions to help identify links. The ip ospf network point-to-point command advertises the proper subnet mask into the routing table.
HQ
int s0/0
desc Link to Main Gate
clock rate 64000
ip add 10.137.88.5 255.255.255.252
no shut
MainGate
int s0/0
desc Link from HQ
ip add 10.137.88.6 255.255.255.252
no shut
int s0/1
ip add 10.137.88.1 255.255.255.252
desc Link to Crash Site
clock rate 64000
no shut
exit
int lo100
ip add 192.168.100.1 255.255.255.252
ip ospf network point-to-point
int lo200
ip add 192.168.100.5 255.255.255.252
ip ospf network point-to-point
int lo300
ip add 192.168.100.9 255.255.255.252
ip ospf network point-to-point
int lo400
ip add 192.168.100.13 255.255.255.252
ip ospf network point-to-point
Icebane
int s0/1
ip add 10.137.88.2 255.255.255.252
desc Link from Main Gate
ip ospf message-digest-key 1 md5 spacewolf
no shut
exit
int lo100
ip add 172.16.16.1 255.255.255.0
ip ospf network point-to-point
int lo101
ip add 172.16.17.1 255.255.255.0
ip ospf network point-to-point
int lo102
ip add 172.16.18.1 255.255.255.0
ip ospf network point-to-point
int lo103
ip add 172.16.19.1 255.255.255.0
ip ospf network point-to-point
int lo104
ip add 172.16.20.1 255.255.255.0
ip ospf network point-to-point
Confirm links are up and up with show ip int br.
MainGate
MainGate(config-router)#do show ip int br
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 unassigned YES unset administratively down down
Serial0/0 10.137.88.6 YES manual up up
FastEthernet0/1 unassigned YES unset administratively down down
Serial0/1 10.137.88.1 YES manual up up
Loopback100 192.168.100.1 YES manual up up
Loopback200 192.168.100.5 YES manual up up
Loopback300 192.168.100.9 YES manual up up
Loopback400 192.168.100.13 YES manual up up
Step 3
Initiate the OSPF Process on the routers. Confirm configuration.
HQ
router ospf 1
router-id 1.1.1.1
network 10.137.88.0 0.0.0.255 area 0
MainGate
router ospf 1
router-id 2.2.2.2
network 10.137.88.0 0.0.0.3 area 252
network 10.137.88.4 0.0.0.3 area 0
network 192.168.100.0 0.0.0.255 area 252
Icebane
router ospf 1
router-id 3.3.3.3
network 10.137.88.0 0.0.0.3 area 252
network 172.16.16.0 0.0.7.255 area 164
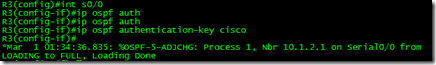
It is important to set the router-id. This comes in handy for a number of things such. Reading outputs and confirming changes in the OSPF process. In our case, we need it set for the Virtual Link to re-establish communication to the Icebane.
Step 4
Configure OSPF Virtual Link between Icebane and MainGate. Communication must be authenticated.
A sense of urgency has frenzied the Orks. We must securely re-establish contact with our brethren. A quick set of commands will allow connectivity to the downed bird.
HQ
int s0/0
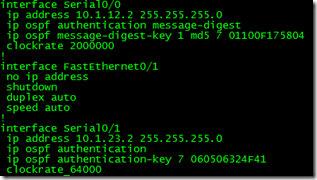
ip ospf message-digest-key 1 md5 spacewolf
router ospf 1
area 0 authentication message-digest
MainGate
int s0/0
ip ospf message-digest-key 1 md5 spacewolf
int s0/1
ip ospf message-digest-key 1 md5 spacewolf
router ospf 1
area 0 authentication message-digest
area 252 authentication message-digest
area 252 virtual-link 3.3.3.3 message-digest-key 1 md5 spacewolf
Icebane
int s0/1
ip ospf message-digest-key 1 md5 spacewolf
router ospf 1
area 0 authentication message-digest
area 164 authentication message-digest
area 252 authentication message-digest
area 252 virtual-link 2.2.2.2 message-digest-key 1 md5 spacewolf
It is extremely important to set this up correctly. Under the OSPF process you must enable area-wide authentication. This is done on each other. In the case of MainGate there is an interface in each area. This means the command must be entered for each area the BDR sits in.
This is demonstrated by the area 0 and area 252 commands.
MD5 must be configured area wide then on the virtual links. The Virtual Links authentication type must match the area authentication type. In this case we need a secure link so we are going to use Message-Digest.
Area 252 virtual-link 3.3.3.3 command on the MainGatec creates the virtual link. On Icebane, it must be configred as 252 virtual-link 2.2.2.2. The reason Icebane uses area 252 is that the virtual link must be configured with the area that it traverses to reach Area 0.
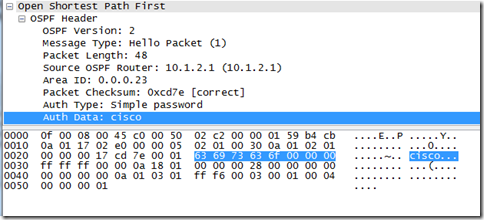
Adding on the message-digest-key 1 md5 spacewolf ensures that the md5 authentication is used on the virtual link. The number 1 stipulates the key #, md5 the type, and the passkey of spacewolf. The passkey is case sensitive.
Under each interface the command ip ospf message-digest-key 1 md5 spacewolf command must be issued. This specifies md5 authentication using key 1 and the type of auth as md5. The use of the passkey spacewolf is used here.
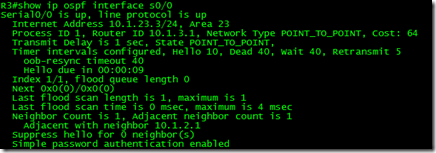
You can confirm the status of the virtual link by issuing the following
MainGate# show ip ospf virtual-links
Virtual Link OSPF_VL0 to router 3.3.3.3 is up
Run as demand circuit
DoNotAge LSA allowed.
Transit area 252, via interface Serial0/1, Cost of using 64
Transmit Delay is 1 sec, State POINT_TO_POINT,
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
Hello due in 00:00:04
Adjacency State FULL (Hello suppressed)
Index 2/3, retransmission queue length 0, number of retransmission 1
First 0x0(0)/0x0(0) Next 0x0(0)/0x0(0)
Last retransmission scan length is 1, maximum is 1
Last retransmission scan time is 0 msec, maximum is 0 msec
Message digest authentication enabled
Youngest key id is 1
The second line states that OSPF_VL0 (the virtual link we set up) to 3.3.3.3 (Icebane) is up. The second last line shows MD5 is being used and the key number 1 which we set to use the passkey of spacewolf is being used.
Step 5
Verify
Now some show commands
Icebane(config-router)#do show ip route
Codes: C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2
i – IS-IS, su – IS-IS summary, L1 – IS-IS level-1, L2 – IS-IS level-2
ia – IS-IS inter area, * – candidate default, U – per-user static route
o – ODR, P – periodic downloaded static route
Gateway of last resort is not set
172.16.0.0/24 is subnetted, 5 subnets
C 172.16.20.0 is directly connected, Loopback104
C 172.16.16.0 is directly connected, Loopback100
C 172.16.17.0 is directly connected, Loopback101
C 172.16.18.0 is directly connected, Loopback102
C 172.16.19.0 is directly connected, Loopback103
10.0.0.0/30 is subnetted, 2 subnets
C 10.137.88.0 is directly connected, Serial0/1
O 10.137.88.4 [110/128] via 10.137.88.1, 00:09:10, Serial0/1
192.168.100.0/24 is variably subnetted, 4 subnets, 2 masks
O 192.168.100.12/30 [110/65] via 10.137.88.1, 00:09:40, Serial0/1
O 192.168.100.8/30 [110/65] via 10.137.88.1, 00:09:40, Serial0/1
O 192.168.100.4/30 [110/65] via 10.137.88.1, 00:09:40, Serial0/1
O 192.168.100.1/32 [110/65] via 10.137.88.1, 00:09:41, Serial0/1
Voila! Connection to area 0 and 252. This is show by the connection to 10.137.88.4 network (Serial link from HQ to MainGate). A quick ping to confirm.
Icebane(config-router)#do ping 10.137.88.5
Sending 5, 100-byte ICMP Echos to 10.137.88.5, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 12/53/88 ms
“Icebane, Icebane, this is Brother Commander Longfang do you copy? We are closing on your position. Hold tight. Over”
A foul stench permeated the air. Blood, Bile and bullet casings were scattered amongst the green tide. The surging sea of Greenskins had been calmed to a pool of death. The sight before the Space Wolves was enough to turn the most seasoned warriors bowels to water. Yet, they moved onwards with a sense of loss setting in.
“Co…Comm…Darius” a meek voice called out in amongst the sea of Orks “Thank you”. It was Captain Jelk of the 2nd Heavy Division. He had been severely injured and desperately required a medic. With communications restored, a Thunderhawk with the Clans Apothecaries arrived on site within minutes and plucked the stranded and injured troops to safety.
Darius surveyed the scene. He muttered to no one in particular, “On the wings of darkness do these Orks ride. Something else gives hast to their passage. Praise Russ that we find them soon.”
February 21, 2011
Categories: Authentication, OSPF, ROUTE, Study . . Author: Anthony Burke . Comments: Leave a comment